What Is Exploit Db
What Is Exploit Db - Web Exploit DB is a widely recognized online public database and platform that provides information about security vulnerabilities exploits and their corresponding proof of concept code The Exploit DB database maintained by Offensive Security contains many vulnerabilities and associated exploits gathered from various sources including Web The Exploit Database is a non profit project that is provided as a public service by OffSec The Exploit Database is a CVE compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers Our aim is to serve the most comprehensive collection of exploits gathered Web Exploit Database EDB The Exploit Database is a CVE compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions mailing lists as well as other public
Look no even more than printable templates if you are looking for a basic and efficient method to increase your efficiency. These time-saving tools are free and easy to utilize, supplying a variety of benefits that can help you get more done in less time.
What Is Exploit Db
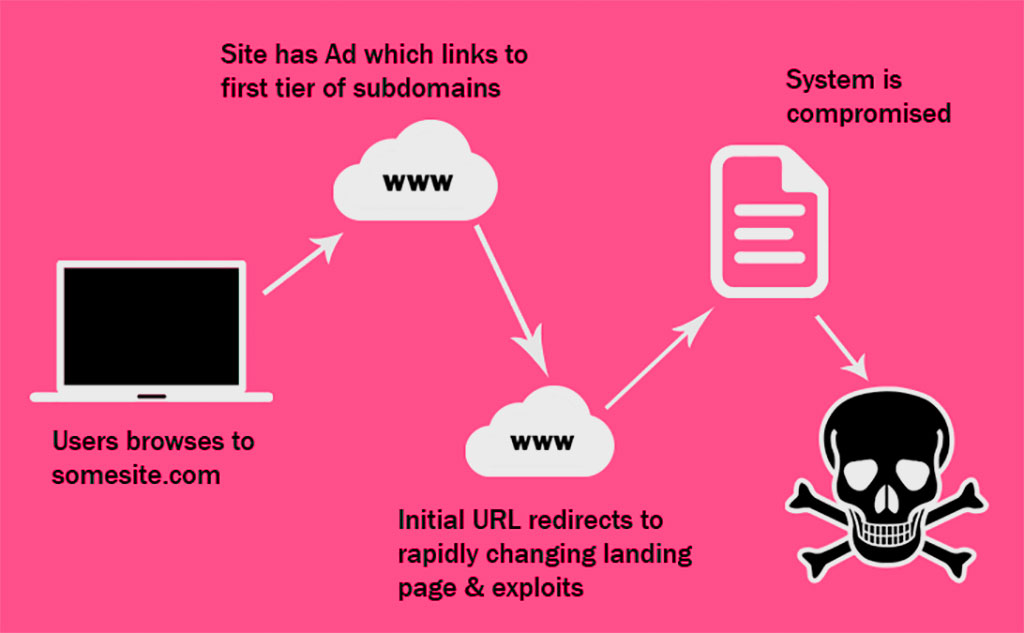
What Is An Exploit Kit Learn How You Can Fight Against Hackers SiteLock
 What Is An Exploit Kit Learn How You Can Fight Against Hackers SiteLock
What Is An Exploit Kit Learn How You Can Fight Against Hackers SiteLock
What Is Exploit Db Printable design templates can assist you stay organized. By providing a clear structure for your jobs, order of business, and schedules, printable design templates make it much easier to keep whatever in order. You'll never have to stress over missing deadlines or forgetting important tasks once again. Utilizing printable templates can help you conserve time. By getting rid of the need to develop brand-new files from scratch each time you need to complete a job or plan an occasion, you can concentrate on the work itself, rather than the paperwork. Plus, numerous templates are adjustable, enabling you to individualize them to match your requirements. In addition to saving time and staying arranged, utilizing printable templates can likewise assist you stay encouraged. Seeing your development on paper can be a powerful incentive, motivating you to keep working towards your goals even when things get tough. In general, printable design templates are a terrific way to boost your efficiency without breaking the bank. So why not provide a shot today and begin attaining more in less time?
0 day Exploits
 0 day exploits
0 day exploits
Web Aug 10 2023 nbsp 0183 32 What Is an Exploit Definition Types and Prevention Measures An exploit is a piece of software or code created to take advantage of a vulnerability and it is not malicious in essence Categories
Web Sep 17 2019 nbsp 0183 32 Simply put exploits are a way of gaining access to a system through a security flaw and taking advantage of the flaw for their benefit in other words to exploit it Exploits normally come by way of a piece of programmed software piece of code or a script They are often delivered as a part of a kit which is a collection of exploits
What Is A Browser Exploit Zero Trust Edge
 What is a browser exploit zero trust edge
What is a browser exploit zero trust edge
Exploit Meaning What Is Exploit What Does Exploit Mean YouTube
 Exploit meaning what is exploit what does exploit mean youtube
Exploit meaning what is exploit what does exploit mean youtube
Free printable templates can be an effective tool for improving efficiency and achieving your objectives. By choosing the right templates, incorporating them into your routine, and individualizing them as required, you can streamline your everyday tasks and maximize your time. Why not give it a try and see how it works for you?
Web The Exploit Database is an archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers
Web Nov 28 2022 nbsp 0183 32 Exploit DB is an excellent repository of known exploits The web interface has powerful search functionality built in that enables us to narrow down our search for exploits by many different criteria The advanced search is especially powerful enabling us to search by author port platform etc