Unethical Data Visualization Examples
Unethical Data Visualization Examples - May 13 2024 nbsp 0183 32 Several ways to overcome these issues include identity and access management mechanisms secure network segmentation continuous monitoring and threat detection systems and authentication and authorization technologies Zero Trust Security must be integrated with edge computing architectures for effective deployment Infrastructure Protect hybrid infrastructure including on premises IT and cloud environments with more efficient and automated management By adopting a Zero Trust framework in one or all of these areas you can effectively modernize your security technology and processes and start to maximize protection in the face of modern threats Secure digital acceleration requires a clear Zero Trust Strategy called Zero Trust Edge which forms a new perimeter that delivers the convergence of security and networking everywhere along with providing explicit access to applications based on
Look no even more than printable design templates in case you are looking for a efficient and easy method to enhance your productivity. These time-saving tools are simple and free to use, providing a variety of benefits that can assist you get more carried out in less time.
Unethical Data Visualization Examples
Principles Of Healthcare Ethics PowerPoint And Google 41 OFF
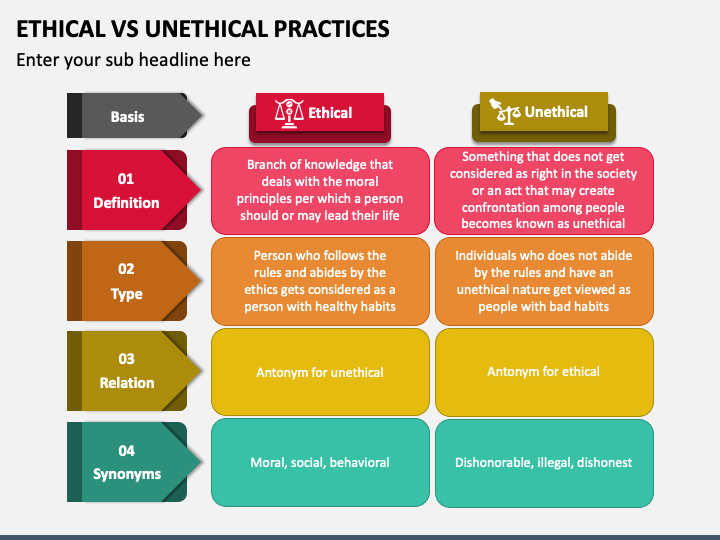 Principles Of Healthcare Ethics PowerPoint And Google 41 OFF
Principles Of Healthcare Ethics PowerPoint And Google 41 OFF
Unethical Data Visualization Examples Printable design templates can help you remain organized. By supplying a clear structure for your tasks, to-do lists, and schedules, printable design templates make it simpler to keep whatever in order. You'll never ever have to stress over missing out on deadlines or forgetting important tasks once again. Using printable templates can help you save time. By eliminating the need to create new files from scratch each time you need to complete a job or prepare an event, you can focus on the work itself, instead of the paperwork. Plus, lots of templates are customizable, enabling you to customize them to fit your needs. In addition to conserving time and staying organized, utilizing printable design templates can likewise help you remain motivated. Seeing your development on paper can be a powerful motivator, motivating you to keep working towards your goals even when things get tough. Overall, printable templates are a terrific method to enhance your performance without breaking the bank. Why not provide them a try today and begin attaining more in less time?
Visualization
 Visualization
Visualization
Jun 9 2023 nbsp 0183 32 Using Zero Trust concepts in multi cloud environments strategies and best practices Improve your security measures with our actionable steps We discuss ways to assess security posture identify assets develop strategy implement technologies and processes Leverage ZTA to create a secure foundation Reading Time 9 minutes
Nov 17 2024 nbsp 0183 32 Fundamental principles of Zero Trust security Organizations must adopt a few foundational principles in order to effectively operationalize Zero Trust within cloud environments 1 Continuous authorization and authentication Zero Trust verifies user and device identity on an ongoing basis when access is sought Simply put every request for access whether from a
GDP plpax
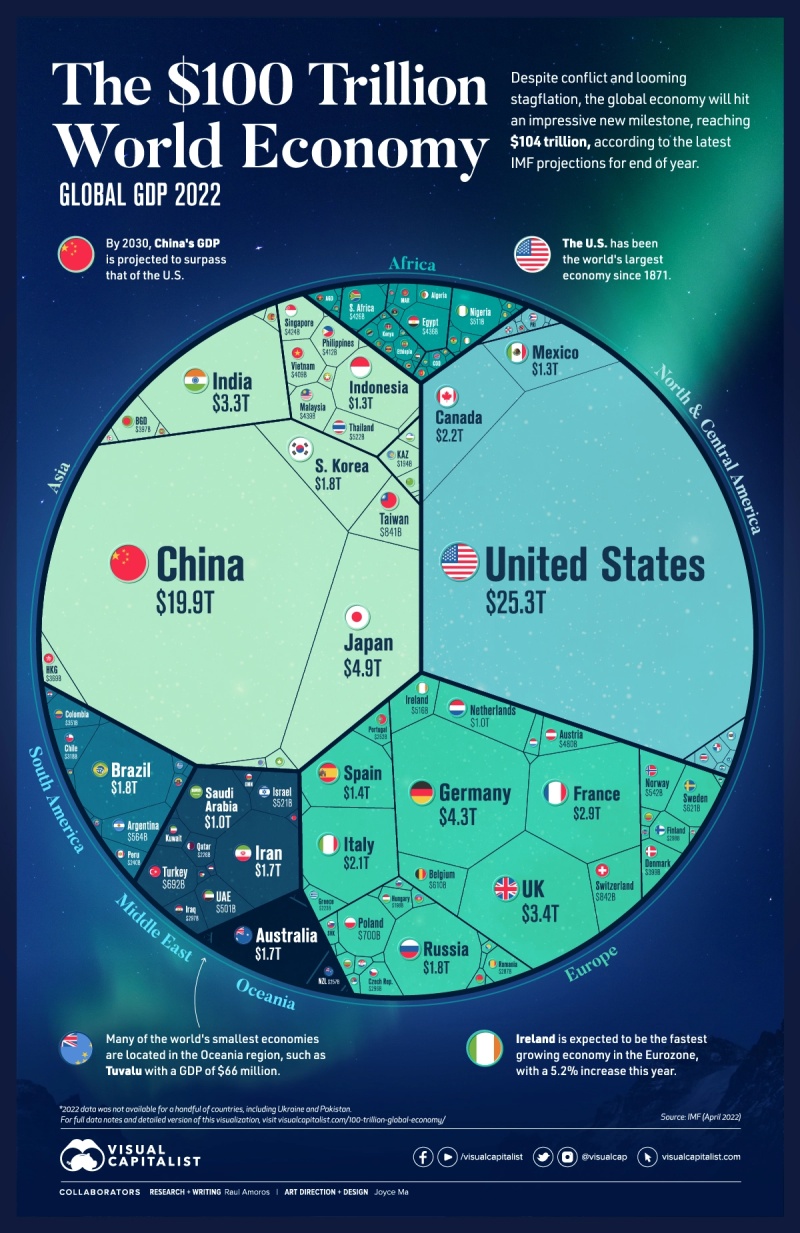 gdp plpax
gdp plpax
Data Visualization J R Webber Data Visualization Design Data
 Data visualization j r webber data visualization design data
Data visualization j r webber data visualization design data
Free printable templates can be an effective tool for increasing productivity and achieving your objectives. By picking the right templates, including them into your routine, and individualizing them as required, you can enhance your day-to-day tasks and take advantage of your time. So why not give it a try and see how it works for you?
Apr 29 2025 nbsp 0183 32 Explore 20 open source tools to implement Zero Trust Architecture across firewalls network segmentation encryption workload identity authentication and authorization layers Enhance security by eliminating implicit trust and enforcing continuous verification at
Here is one approach to how you can start your journey to Zero Trust maturity Application and asset discovery Before you can adequately secure your environments in the cloud or otherwise you need to identify everything within its reach This step involves taking inventory of your most sensitive data where it resides and where it goes