5 Stages Of Ethical Hacking
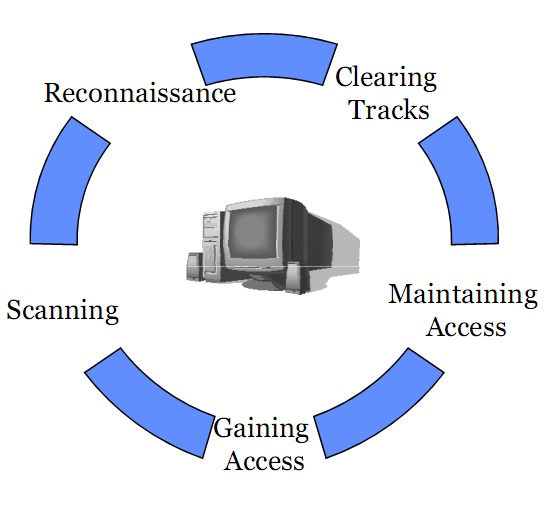
5 Stages Of Ethical Hacking - Web Oct 22 2021 nbsp 0183 32 What are the Phases of Ethical Hacking 1 Reconnaissance When it comes to penetration testing the first natural question is What is the first hacking 2 Scanning In this stage the ethical hacker begins testing the networks and machines to identify potential attack 3 Gaining Access Web May 23 2023 nbsp 0183 32 In this blog post we will explore the five phases of ethical hacking reconnaissance scanning gaining access maintaining access and clearing tracks We will provide a clear understanding of each phase along with practical examples while also discussing the concepts of hacking and ethical hacking Topics Covered What is Web Sep 20 2023 nbsp 0183 32 Following are the five main types of Ethical Hacking External The external method includes the website web applications e mails and domain name servers These are the things that are the external source of an organization and the hackers try to get the entrance from them to extract sensitive data
Look no further than printable templates in case that you are looking for a efficient and basic method to increase your performance. These time-saving tools are free-and-easy to use, supplying a range of benefits that can help you get more carried out in less time.
5 Stages Of Ethical Hacking
5 PHASES OF ETHICAL HACKING TheInfology
 5 PHASES OF ETHICAL HACKING TheInfology
5 PHASES OF ETHICAL HACKING TheInfology
5 Stages Of Ethical Hacking To start with, printable templates can help you remain organized. By providing a clear structure for your jobs, order of business, and schedules, printable design templates make it simpler to keep everything in order. You'll never ever need to stress over missing due dates or forgetting important tasks once again. Utilizing printable templates can help you conserve time. By eliminating the need to produce new files from scratch each time you require to complete a task or plan an event, you can concentrate on the work itself, instead of the documents. Plus, numerous design templates are customizable, permitting you to customize them to suit your needs. In addition to conserving time and staying arranged, utilizing printable design templates can likewise help you stay motivated. Seeing your development on paper can be a powerful incentive, motivating you to keep working towards your objectives even when things get hard. In general, printable templates are a fantastic method to increase your productivity without breaking the bank. Why not offer them a try today and begin attaining more in less time?
Hacking Phases The Hacker s Library
 Hacking phases the hacker s library
Hacking phases the hacker s library
Web Mar 28 2023 nbsp 0183 32 This article explains the 5 steps of Hacking taking an example of a Hacker trying to hack a company s server and gaining access to all the data Phases of ethical hacking The process of legal and authorized attempts to discover and successfully exploiting the computer system in an attempt to make the computer system more secure
Web Jan 29 2021 nbsp 0183 32 The phases of ethical hacking are The Reconnaissance Phase The Scanning Phase The Gaining Access Phase The Maintaining Access Phase The Covering of Tracks Phase
Ethical Hacking 2022 Why The Companies Pay For Getting Hacked
 Ethical hacking 2022 why the companies pay for getting hacked
Ethical hacking 2022 why the companies pay for getting hacked
Phases Of Hacking 5 Stages Of Ethical Hacking MeuSec
 Phases of hacking 5 stages of ethical hacking meusec
Phases of hacking 5 stages of ethical hacking meusec
Free printable design templates can be an effective tool for improving efficiency and achieving your objectives. By choosing the right design templates, including them into your routine, and individualizing them as needed, you can simplify your everyday tasks and maximize your time. So why not give it a try and see how it works for you?
Web Oct 3 2023 nbsp 0183 32 In a webinar on five phases of ethical hacking hosted by Simplilearn Kevin King director of technical innovation at EC Council described how hackers exploit vulnerabilities and compromise security controls to gain unauthorized access to system resources in an organization
Web Jul 30 2021 nbsp 0183 32 The steps an ethical hacker follows can be broadly distributed into the following 5 phases Phase 1 Reconnaissance The first and important phase of ethical hacking is reconnaissance Reconnaissance means exploring the target to gain as much information about it as possible More target information will result in easier access to the